Understanding Merkle Proofs in Blockchain Technology

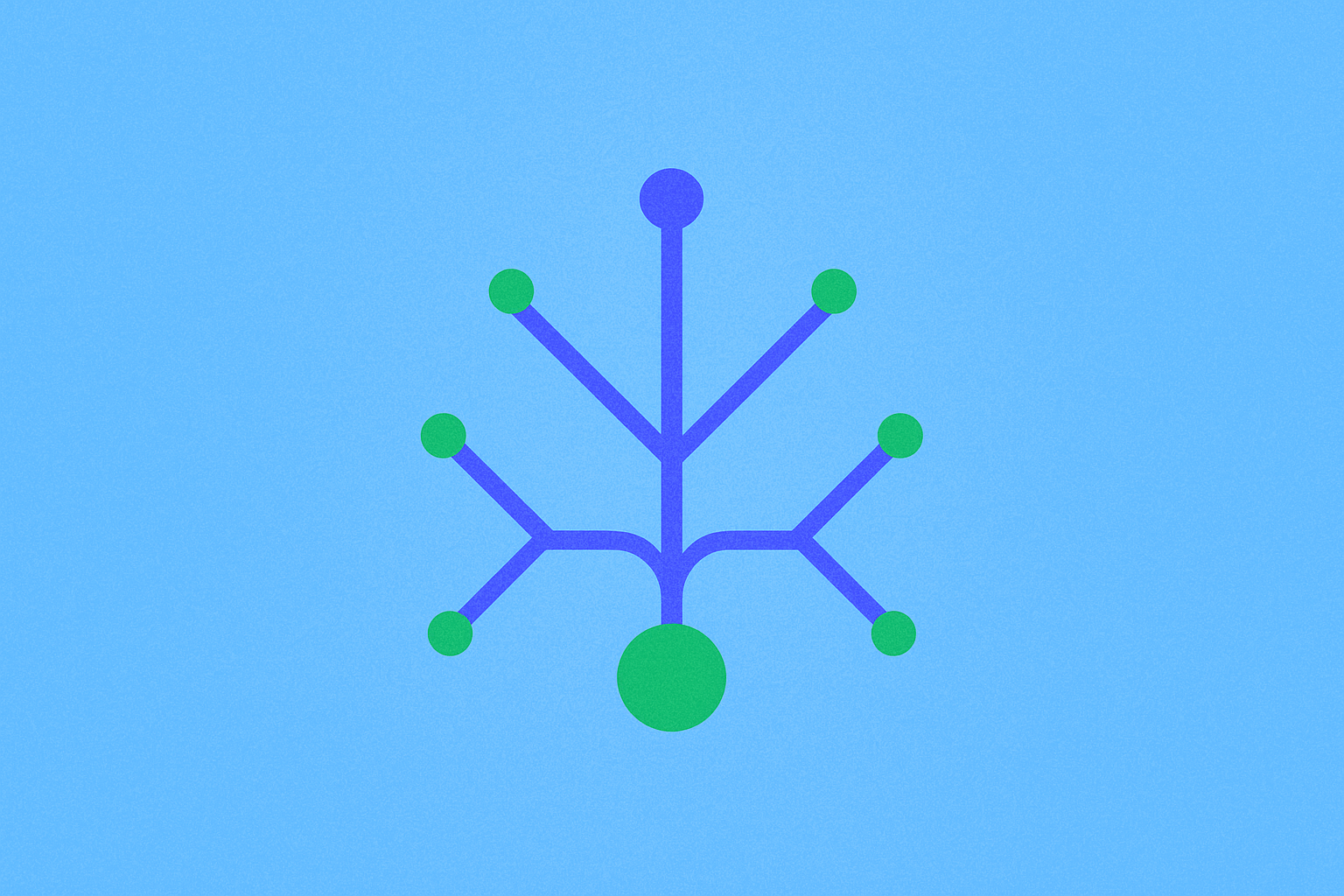
What are Merkle trees and how do they enable Proof of Reserves?
Merkle trees represent a fundamental cryptographic structure that enables verification and security in blockchain technology. Understanding how Merkle trees function is essential to comprehending how modern cryptocurrency exchanges can prove their reserves and maintain transparency with their users through merkle proof mechanisms.
First, what's a "hash"?
A hash serves as the foundational building block of blockchain security and Merkle tree structures. At its core, a hash is a unique, immutable sequence composed of both numbers and letters, generated through a cryptographic process from a data set of any length and size. In blockchain contexts, this data set can theoretically be infinite in scope.
The cryptographic hash function plays a crucial role in maintaining blockchain integrity. When a new block is added to a blockchain, it becomes intrinsically linked to the existing block preceding it through this hash function. The function generates transaction data from each block into a unique string of text that cannot be altered without simultaneously altering the preceding block's hash value and consequently the entire historical record of the blockchain.
This property creates a fundamental security principle: altering any component of the data set will inevitably alter its corresponding hash. The process operates unidirectionally—once data is converted into a hash, it cannot be reverse-engineered to reveal the original source information. This mechanism forms the basis of blockchain's cryptographic nature, making the input data substantially more secure against unauthorized decryption attempts.
The cryptographic hash function enables blockchains to maintain immutability and remain tamper-proof because every block maintains intrinsic connections to both preceding and subsequent blocks. Within cryptocurrency transactions, a Transaction Hash (Tx Hash) functions as a unique identifier generated by each transaction, serving as cryptographic proof that the transaction has been validated and permanently added to the blockchain ledger.
Then what's a Merkle Tree?
Patented by Ralph Merkle in 1979, a Merkle Tree represents an innovative application of hash functions, creating what is essentially a hash 'tree' structure. This invention addresses a critical efficiency challenge in decentralized networks.
When initiating a transaction on a decentralized, peer-to-peer network, any modifications to the blockchain require verification for consistency across all participating networks. Without an efficient transaction hash function, networks would need to continuously validate every transaction on the blockchain—a process that would prove tremendously inefficient and impractical at scale.
To illustrate this concept through a practical analogy, imagine operating an ice cream shop where you need to calculate January's profit and loss totals. As you manually tally losses (such as payroll expenses) and profits (such as customer payments) using pen and paper, you discover an input error regarding cream and sugar purchases on January 5th. Correcting this single transaction would necessitate recalculating all subsequent computations through the month's end—a daunting and highly inefficient process.
Extending this analogy, a cryptographic hash function operates similarly to Excel or specialized accounting software, enabling real-time updates when any numerical input changes, without requiring manual recalculation of the entire balance ledger. However, instead of altered numerical inputs changing a numerical total, the transaction hash (Tx Hash) transforms into a different randomized sequence reflecting changes to blockchain transactions. This demonstrates the practical value of hash functions, specifically the Merkle Tree structure.
Operating like a sophisticated password generator, data converts into a randomized alpha-numerical sequence (the hash) and links to its corresponding blockchain transaction, creating a hash 'tree' or Merkle tree. Merkle trees can rapidly verify data transferred between computers in peer-to-peer networks by ensuring blocks transmitted between peers arrive unaltered and undamaged.
Within cryptocurrency systems, a Merkle Tree consists of leaves or leaf nodes—these are actually hashes representing blocks of data, such as blockchain transactions. Nodes positioned toward the tree's apex are hashes of their respective children. For instance, hash 1 represents the combination of the two hashes positioned below it on the tree structure (Hash 1 = Hash(hash 1-0 + Hash 1-1)).
At the very top of the tree sits what is called the Top Hash, also known as the root. The Top Hash enables any portion of the hash tree to be received from untrusted sources, such as peer-to-peer networks. Subsequently, any received branch—representing a new blockchain transaction—can be checked against the trusted top hash for verification purposes, determining whether the hash has been damaged or falsified by malicious actors. This verification process is fundamentally what constitutes a merkle proof.
Essentially, instead of transmitting an entire file across the network, only a hash of the file needs transmission, which can then be checked against the Top Hash to verify its integrity. This mechanism partially defines cryptocurrency as a 'trustless' system, removing the need for intermediary trust relationships.
What are Proof of Reserves?
Traditional financial accounting employs a record system consisting of ledgers, records, and balance sheets—similar to the earlier ice cream shop example. All financial records undergo review and verification by third-party auditors who flag discrepancies and validate books only after resolving any inconsistencies.
However, decentralized platforms operate without third-party auditors or human intermediaries balancing incoming and outgoing transactions. This raises critical questions: If you deposit one ETH to a centralized platform, how can you verify your deposit remains intact over time? How can you trust the platform won't utilize your deposited funds for alternative purposes? The balance displayed on your screen may prove insufficient assurance—and rightfully so.
While numerous blockchain explorers exist, history demonstrates these aren't always sufficiently transparent to protect against bad actors. The viable, long-term solution benefiting token holders rather than platforms involves implementing Merkle Trees and Proof of Reserves protocols with comprehensive merkle proof verification.
Driven by the objective of alleviating customer concerns about crypto funds held in centralized platforms, many exchanges have launched Proof of Reserves protocols. Proof of Reserves constitutes a comprehensive report of crypto assets ensuring the custodian actually holds the assets it claims to hold on behalf of users.
Platforms utilize the Merkle tree (hash tree) structure to prove this claim through two distinct verification methods. First, users can locate their balance within the tree structure and prove their assets are included in the total balance through merkle proof verification. Second, the total balance undergoes comparison with the publicly disclosed on-chain wallet balance to establish definitive Proof of Reserves.
By employing the Merkle Tree to display immutable transaction data and demonstrate that information hasn't been tampered with through cryptographic hash mechanisms and merkle proof, customers can maintain confidence that their assets are held on a 1:1 basis, with complete transparency and verifiable security.
Conclusion
Merkle trees represent a cornerstone technology enabling transparency and trust in cryptocurrency systems. Through cryptographic hash functions and merkle proof mechanisms, these structures provide an efficient mechanism for verifying data integrity across decentralized networks without requiring continuous validation of entire blockchain histories. The implementation of Merkle trees in Proof of Reserves protocols addresses fundamental trust concerns in centralized platforms, allowing users to independently verify through merkle proof that their assets are properly custodied. As the cryptocurrency ecosystem continues evolving, Merkle trees, merkle proof verification, and Proof of Reserves remain essential tools for maintaining transparency, security, and user confidence in digital asset custody solutions.
FAQ
How to generate Merkle proof?
Create a Merkle tree by hashing data leaves, then recursively hash pairs upward to the root. Generate proof by collecting sibling hashes along the path from your target leaf to the root node.
What is Merkle proof of inclusion?
A Merkle proof of inclusion verifies that a specific data item belongs to a Merkle tree by providing hash links to the root. It confirms data integrity and inclusion without revealing actual data, widely used in blockchains to validate transactions efficiently.
What is the meaning of Merkle?
Merkle refers to a cryptographic tree structure used in blockchain technology to efficiently verify large data sets. It organizes data into a hash tree, allowing quick verification of data integrity through a single root hash. Named after Ralph Merkle, it's fundamental to blockchain security and enables SPV wallets.
What is a Merkle used for?
Merkle Trees verify data integrity efficiently by combining multiple data points into a single hash. They enable quick validation of transactions and data without reviewing all individual data points, making them essential for blockchain technology.

Cryptography: From Ancient Ciphers to Blockchain. The Complete Guide to Information Security in the Digital Age
Introduction to Cryptography: A Beginner's Guide

Understanding Merkle Proofs in Blockchain Technology
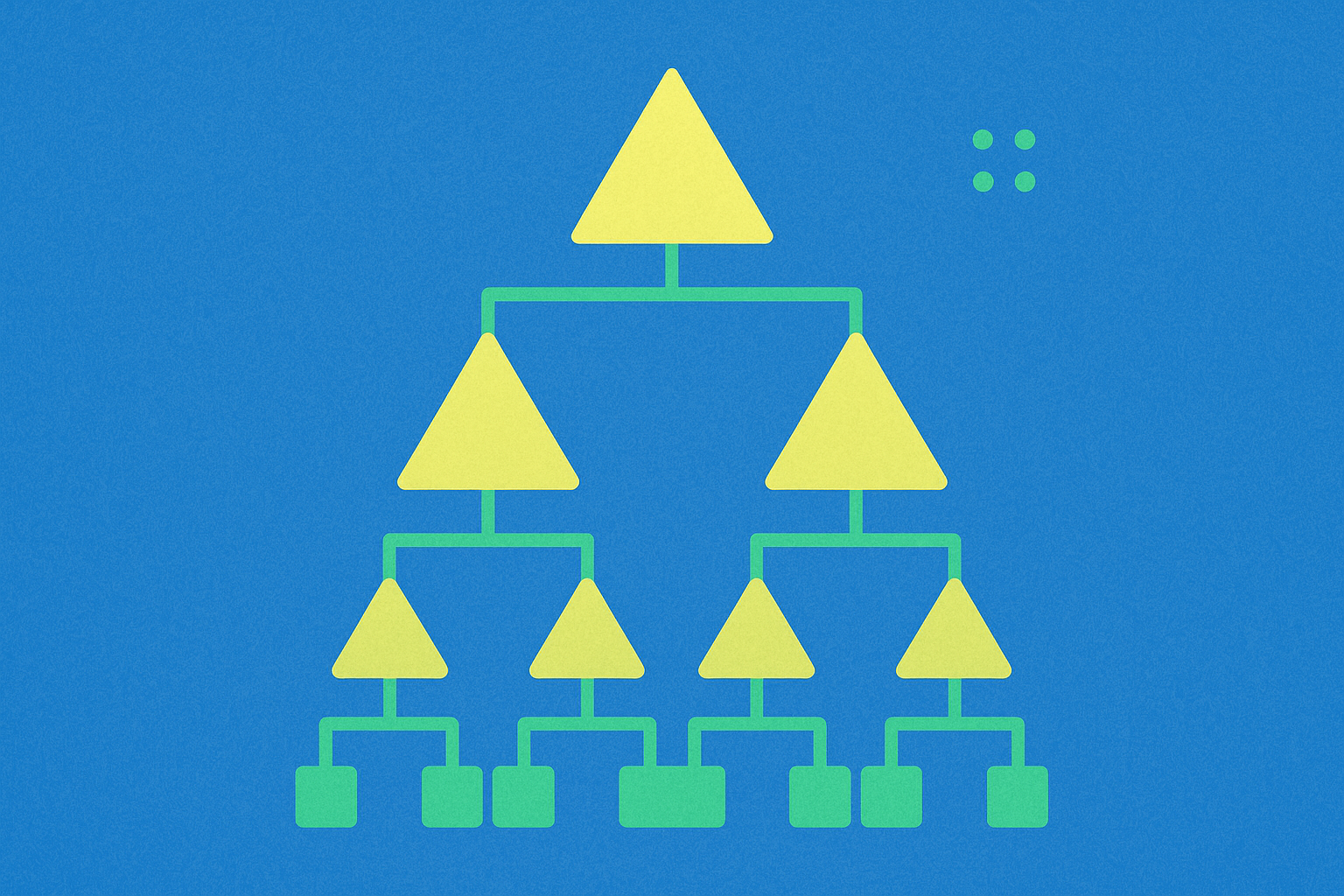
Understanding Merkle Tree Proofs in Blockchain Technology

Understanding Cryptography: Essential Concepts for Blockchain Security

Enhancing Security in Blockchain Networks with Cryptography Techniques
What is Fuel Network (FUEL)? Everything You Need to Know about FUEL
Zora (ZORA) Airdrop Guide: Participation Steps, Reward Collection, and Price Predictions

What Is BNB Chain?
All You Need To Know About Yescoin

How to Buy Baron ($BARRON) Coin: What is Baron Trump Cryptocurrency?
